Data Security: Risks, Solutions, Types and Best Practices
Jigar Gupta
Oct 21, 2024




In a world where technology shapes our daily lives, data security is more important than ever. With the augmenting amount of sensitive data stored and transmitted electronically, safeguarding this data from illicit access, breaches, and loss is paramount. This guide delves into the significance of data security, exploring the various types, common risks, efficient solutions, and best practices.
Introduction to Data Security
Data security is more vital than ever before. In today’s digital synopsis, your personal and professional data faces innumerable risks from cybercriminals and data infringement. You must prioritize safeguarding your information to avoid potential financial losses, legal consequences, and reputational damage.
Importance of Data Security
Ensuring your data is secure safeguards your seclusion, your firm’s notoriety and financial solidity. By using powerful data security measures, you can protect sensitive data against illicit access, theft, and detriment. This dynamic approach averts expensive breaches and helps maintain trust with your customers and stakeholders.
Overview of Risks, Solutions, Types, and Best Practices
Comprehending the risks associated with data security is the initial step towards efficient security. Cyber threats such as hacking, phishing, and malware can compromise your information. But don’t worry; there are solutions attainable to oppose these risks.
Types of Data Security Solutions: These include encryption, firewalls, and antivirus software. Only authorized parties can read your information with encryption, while firewalls block illicit access to your network. Antivirus software discovers and excludes vicious software.
Best Practices in Data Security: It includes frequent updates to your software, strong password policies, and employee training. Frequently updating your software to patch vulnerabilities, implementing strong password policies, and providing employee training ensures everyone is aware of potential risks and how to handle them.
By comprehending and enforcing these gauges, you can substantially improve your data security and protect your valuable data from potential threats.
Ready to dive deeper? Let’s explore the different types of data security measures to see how they can shield your information.
Looking for insights on improving your entity's security posture? Don't miss our thorough guide on Security and LLM Firewall Controls.
Types of Data Security
Data is the key to your entity’s success and if that is not safe, then it’s a big blow for the organization. That is why keeping your information safe is very important in today’s digital synopsis. Here are some key types of security gauges you can use:
Each type of data security contributes to creating a pragmatic security strategy. By comprehending and enforcing these gauges, entities can substantially reduce the risk of data breaches and ensure the integrity, confidentiality, and attainability of their data.
So, now that we know what types of security measures are out there let’s talk about the villains—common data security risks—that we need to protect against.
Prying about improving your RAG applications? Explore the power of using synthetic data to enrich RAG applications and revolutionize your AI models today!
Common Data Security Risks
Safeguarding your data isn't just a technical necessity; it's a rudimentary aspect of protecting your venture and personal data. With cyber threats becoming more sophisticated, comprehending common data security risks is vital. Whether you're a small business owner, an IT professional, or simply an individual going through the online world, staying informed about potential susceptibilities can help you enforce efficient security measures.
Ignorance isn't a delight when it comes to data security. The more you know about the risks, the better prepared you'll be to avert breaches and safeguard your sensitive data.
Below are numerous common problems faced by entities of all sizes as they attempt to safeguard sensitive information:
Human Error
Human error is one of the leading causes of data security issues. You might arbitrarily send sensitive data to the wrong recipient, misconfigure a security setting, or fall for a phishing email. It's vital to stay alert and double-check your actions to avert such mistakes.
Social Engineering Attacks
Social engineering attacks, mainly phishing, are designed to trick you into uncovering confidential data. Hackers often pose as legal organizations to gain your trust. Always validate the genuineness of unanticipated requests for sensitive information, and never click on dubious links.
Insider Threats
Insider threats can come from employees or contractors who misuse their access to your systems. This could be due to vicious intent or because an external attacker has compromised them. Frequently retrospect and restrict access to sensitive data and monitor for unusual activity.
Ransomware
Ransomware is a type of vicious software that encrypts your data and demands payment for its release. To safeguard yourself, keep your software updated, back up your data frequently, and train employees to determine dubious emails and links.
Data Loss in the Cloud
Storing data in the cloud comes with its own set of threats, including potential information loss due to misconfigurations, cyber-attacks, or service outages. Ensure you have powerful security measures in place, such as encryption and access controls, and always back up your data.
SQL Injection
SQL injection is a method where attackers insert malicious SQL code into your database queries. This can give them access to sensitive information or permit them to exploit your database. Avert this by using parameterized queries and input verification to ensure that your systems only process legal requests.
Did you get a sense of the risks? Great, let’s look into some solid solutions to fend off those pesky threats.
Want to know about Tabular Data Models? Read our comprehensive guide on the Importance of Accuracy and Reliability in Tabular Data Models.
Data Security Solutions
With cyber threats continuously developing, comprehending and enforcing powerful data security solutions is necessary to safeguard sensitive data and maintain customer trust. By assimilating comprehensive security gauges, you can ensure that your data remains confidential, maintains its integrity, and is always attainable when required.
Let’s learn about the key data security solutions that will help you bolster your defenses and keep your venture protected.
Data Encryption
When you send a secret message to a friend, you wouldn’t want anyone else to read it, right? That’s exactly what data encryption does for your data. Encryption converts your data into a code to avert illicit access. Methods such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are common. By using strong encryption, you ensure that even if data is seized, it remains unreadable without the decryption key. It’s like having a digital lock and key for your sensitive data.
Identity and Access Management
Who can access your information? Managing identities and access is vital. With Single Sign-On (SSO), you log in once and access multiple applications without re-entering credentials. This refines your experience and improves security. Multi-factor authentication (MFA) adds an auxiliary layer of protection by needing multiple validation techniques, such as a password and a fingerprint. Enforcing SSO and MFA ensures that only authorized individuals access your information, reducing the risk of infringement.
Data Masking
Ever wondered how firms safeguard sensitive data during testing and analysis? Data masking is the response. It supersedes sensitive information with functional but sensible information. Static masking and dynamic masking are two techniques used. Static masking permanently changes sensitive data in non-production environments, whereas dynamic masking hides data on-the-fly during access without altering the original data. This keeps your actual information secure while still permitting essential work to be done.
Data Loss Prevention (DLP)
Losing information can be ruinous. That’s where Data Loss Prevention (DLP) comes in. DLP methods monitor and control the data flow within your entity. Tools such as Symantec DLP and McAfee Total Protection for Data Loss Prevention help you identify, monitor, and safeguard your sensitive data. By enforcing DLP, you avert inadvertent or vicious data leaks, ensuring your data remains protected.
Security Audits
Think of security audits as a health check-up for your data security systems. Frequent security audits help you identify vulnerabilities and weaknesses. By performing these audits, you can locate and solve potential security problems before they become major issues. Tools such as Nessus and Qualys assist in scanning and reporting vulnerabilities. Staying dynamic with security audits ensures that your defenses are always up to date.
Endpoint Security
With remote work on the rise, safeguarding endpoints has never been more significant. Endpoints are devices such as laptops, tablets, and smartphones that connect to your network. Solutions like antivirus software, firewalls, and VPNs safeguard these devices. For remote work and Bring Your Own Device (BYOD) policies, ensure that you have thorough endpoint security in place to safeguard your network from potential threats.
Incident Response
What if a security infringement occurs? Having a solid incident response strategy is vital. Incident response involves preparing, detecting, and responding to security breaches. Develop a plan that includes roles, communication conventions, and recovery steps. Tools like Splunk and IBM Resilient can assist in managing incidents. A well-prepared incident response strategy minimizes damage and helps you recover quickly from breaches.
Governance, Risk, and Compliance (GRC)
Ensuring your data security practices comply with regulations is important. Governance, Risk, and Compliance (GRC) frameworks help you handle this. Governance sets the policies and procedures, risk management identifies and mitigates risks, and compliance ensures adherence to laws and standards. Tools like RSA Archer and SAP GRC streamline these processes. By enforcing GRC, you maintain a powerful security posture while meeting regulatory demands.
Clasp these data security solutions to safeguard your data efficiently and ensure your venture remains secure in an ever-evolving digital scenario.
Think that covers the basics? Let’s drill down into some best practices that you can start implementing today to keep your data airtight.
Data Security Best Practices
With cyber threats continuously emerging, safeguarding your information has never been more critical. The implications of a breach can be severe, impacting everything from your reputation to your bottom line.
Whether you’re running a small venture or managing a large venture, comprehending and enforcing data security best practices is necessary to secure your sensitive data. Let’s learn about some pragmatic steps you can take to safeguard your information and ensure your entity’s security.
Defining Sensitive Data
Comprehending what entitles sensitive information in your entity is important. Begin by measuring the types of information you manage and their sensitivity levels. Make sure you have luminosity into where this data resides and how it flows within your systems. This step is crucial to safeguarding your information efficiently.
Establishing a Cybersecurity Policy
Create a powerful cybersecurity policy that abstracts how information should be used and safeguarded within your entity. This policy should cover everything from password management to information-sharing conventions. Appoint a Data Protection Officer (DPO) to regulate compliance and ensure everyone follows these instructions.
Building an Incident Response Plan
Prepare for the worst by having a rigid circumstance response plan in place. This plan should detail how to manage data infringement, cyber-attacks, and other security occurring. Make sure your team knows how to answer rapidly to alleviate detriment and recover from occurring efficiently.
Ensuring Secure Data Storage
Storing data safely is non-negotiable. Use encryption to safeguard sensitive information both at rest and in transit. Frequently backup your information to ensure you can recover it in case of loss or corruption. Secure data storage safeguards against illicit access and data infringement.
Limiting Access
Not everyone requires access to all information. Enforce access controls to ensure that employees only have access to the data they require to perform their jobs. Follow the principle of least advantage to minimize the risk of illicit data access.
Continuous Monitoring
Observe user activity within your systems. Continuous monitoring helps you identify suspicious behavior and potential security risks early. Use user activity monitoring solutions to track and dissect actions, ensuring your information remains safe.
Managing Third-Party Risks
Your data security elongates to third-party vendors and partners. Frequently observe their activities and hold them liable for their security practices. Ensure they follow your cybersecurity policies to safeguard your information from external risks.
By following these best practices, you can substantially improve your entity's data security, safeguard sensitive data, and minimize the risk of cyber threats.
Feeling a bit more secure now? Let’s wrap things up with a quick recap of what we’ve learned and why it matters.
Conclusion
Data security is an ever-evolving field needing constant alertness and adjustment. By comprehending the numerous types of data security, determining common risks, enforcing effective solutions, and following best practices, you can safeguard your sensitive data and maintain trust with your clients and stakeholders. Stay informed about the latest trends to keep your data security gauges latest and powerful.
Sign up at RagaAI now to receive expert insights, advanced security tools, and exclusive updates straight to your inbox. Empower your venture with the knowledge and resources needed to stay secure in the digital age.
In a world where technology shapes our daily lives, data security is more important than ever. With the augmenting amount of sensitive data stored and transmitted electronically, safeguarding this data from illicit access, breaches, and loss is paramount. This guide delves into the significance of data security, exploring the various types, common risks, efficient solutions, and best practices.
Introduction to Data Security
Data security is more vital than ever before. In today’s digital synopsis, your personal and professional data faces innumerable risks from cybercriminals and data infringement. You must prioritize safeguarding your information to avoid potential financial losses, legal consequences, and reputational damage.
Importance of Data Security
Ensuring your data is secure safeguards your seclusion, your firm’s notoriety and financial solidity. By using powerful data security measures, you can protect sensitive data against illicit access, theft, and detriment. This dynamic approach averts expensive breaches and helps maintain trust with your customers and stakeholders.
Overview of Risks, Solutions, Types, and Best Practices
Comprehending the risks associated with data security is the initial step towards efficient security. Cyber threats such as hacking, phishing, and malware can compromise your information. But don’t worry; there are solutions attainable to oppose these risks.
Types of Data Security Solutions: These include encryption, firewalls, and antivirus software. Only authorized parties can read your information with encryption, while firewalls block illicit access to your network. Antivirus software discovers and excludes vicious software.
Best Practices in Data Security: It includes frequent updates to your software, strong password policies, and employee training. Frequently updating your software to patch vulnerabilities, implementing strong password policies, and providing employee training ensures everyone is aware of potential risks and how to handle them.
By comprehending and enforcing these gauges, you can substantially improve your data security and protect your valuable data from potential threats.
Ready to dive deeper? Let’s explore the different types of data security measures to see how they can shield your information.
Looking for insights on improving your entity's security posture? Don't miss our thorough guide on Security and LLM Firewall Controls.
Types of Data Security
Data is the key to your entity’s success and if that is not safe, then it’s a big blow for the organization. That is why keeping your information safe is very important in today’s digital synopsis. Here are some key types of security gauges you can use:
Each type of data security contributes to creating a pragmatic security strategy. By comprehending and enforcing these gauges, entities can substantially reduce the risk of data breaches and ensure the integrity, confidentiality, and attainability of their data.
So, now that we know what types of security measures are out there let’s talk about the villains—common data security risks—that we need to protect against.
Prying about improving your RAG applications? Explore the power of using synthetic data to enrich RAG applications and revolutionize your AI models today!
Common Data Security Risks
Safeguarding your data isn't just a technical necessity; it's a rudimentary aspect of protecting your venture and personal data. With cyber threats becoming more sophisticated, comprehending common data security risks is vital. Whether you're a small business owner, an IT professional, or simply an individual going through the online world, staying informed about potential susceptibilities can help you enforce efficient security measures.
Ignorance isn't a delight when it comes to data security. The more you know about the risks, the better prepared you'll be to avert breaches and safeguard your sensitive data.
Below are numerous common problems faced by entities of all sizes as they attempt to safeguard sensitive information:
Human Error
Human error is one of the leading causes of data security issues. You might arbitrarily send sensitive data to the wrong recipient, misconfigure a security setting, or fall for a phishing email. It's vital to stay alert and double-check your actions to avert such mistakes.
Social Engineering Attacks
Social engineering attacks, mainly phishing, are designed to trick you into uncovering confidential data. Hackers often pose as legal organizations to gain your trust. Always validate the genuineness of unanticipated requests for sensitive information, and never click on dubious links.
Insider Threats
Insider threats can come from employees or contractors who misuse their access to your systems. This could be due to vicious intent or because an external attacker has compromised them. Frequently retrospect and restrict access to sensitive data and monitor for unusual activity.
Ransomware
Ransomware is a type of vicious software that encrypts your data and demands payment for its release. To safeguard yourself, keep your software updated, back up your data frequently, and train employees to determine dubious emails and links.
Data Loss in the Cloud
Storing data in the cloud comes with its own set of threats, including potential information loss due to misconfigurations, cyber-attacks, or service outages. Ensure you have powerful security measures in place, such as encryption and access controls, and always back up your data.
SQL Injection
SQL injection is a method where attackers insert malicious SQL code into your database queries. This can give them access to sensitive information or permit them to exploit your database. Avert this by using parameterized queries and input verification to ensure that your systems only process legal requests.
Did you get a sense of the risks? Great, let’s look into some solid solutions to fend off those pesky threats.
Want to know about Tabular Data Models? Read our comprehensive guide on the Importance of Accuracy and Reliability in Tabular Data Models.
Data Security Solutions
With cyber threats continuously developing, comprehending and enforcing powerful data security solutions is necessary to safeguard sensitive data and maintain customer trust. By assimilating comprehensive security gauges, you can ensure that your data remains confidential, maintains its integrity, and is always attainable when required.
Let’s learn about the key data security solutions that will help you bolster your defenses and keep your venture protected.
Data Encryption
When you send a secret message to a friend, you wouldn’t want anyone else to read it, right? That’s exactly what data encryption does for your data. Encryption converts your data into a code to avert illicit access. Methods such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are common. By using strong encryption, you ensure that even if data is seized, it remains unreadable without the decryption key. It’s like having a digital lock and key for your sensitive data.
Identity and Access Management
Who can access your information? Managing identities and access is vital. With Single Sign-On (SSO), you log in once and access multiple applications without re-entering credentials. This refines your experience and improves security. Multi-factor authentication (MFA) adds an auxiliary layer of protection by needing multiple validation techniques, such as a password and a fingerprint. Enforcing SSO and MFA ensures that only authorized individuals access your information, reducing the risk of infringement.
Data Masking
Ever wondered how firms safeguard sensitive data during testing and analysis? Data masking is the response. It supersedes sensitive information with functional but sensible information. Static masking and dynamic masking are two techniques used. Static masking permanently changes sensitive data in non-production environments, whereas dynamic masking hides data on-the-fly during access without altering the original data. This keeps your actual information secure while still permitting essential work to be done.
Data Loss Prevention (DLP)
Losing information can be ruinous. That’s where Data Loss Prevention (DLP) comes in. DLP methods monitor and control the data flow within your entity. Tools such as Symantec DLP and McAfee Total Protection for Data Loss Prevention help you identify, monitor, and safeguard your sensitive data. By enforcing DLP, you avert inadvertent or vicious data leaks, ensuring your data remains protected.
Security Audits
Think of security audits as a health check-up for your data security systems. Frequent security audits help you identify vulnerabilities and weaknesses. By performing these audits, you can locate and solve potential security problems before they become major issues. Tools such as Nessus and Qualys assist in scanning and reporting vulnerabilities. Staying dynamic with security audits ensures that your defenses are always up to date.
Endpoint Security
With remote work on the rise, safeguarding endpoints has never been more significant. Endpoints are devices such as laptops, tablets, and smartphones that connect to your network. Solutions like antivirus software, firewalls, and VPNs safeguard these devices. For remote work and Bring Your Own Device (BYOD) policies, ensure that you have thorough endpoint security in place to safeguard your network from potential threats.
Incident Response
What if a security infringement occurs? Having a solid incident response strategy is vital. Incident response involves preparing, detecting, and responding to security breaches. Develop a plan that includes roles, communication conventions, and recovery steps. Tools like Splunk and IBM Resilient can assist in managing incidents. A well-prepared incident response strategy minimizes damage and helps you recover quickly from breaches.
Governance, Risk, and Compliance (GRC)
Ensuring your data security practices comply with regulations is important. Governance, Risk, and Compliance (GRC) frameworks help you handle this. Governance sets the policies and procedures, risk management identifies and mitigates risks, and compliance ensures adherence to laws and standards. Tools like RSA Archer and SAP GRC streamline these processes. By enforcing GRC, you maintain a powerful security posture while meeting regulatory demands.
Clasp these data security solutions to safeguard your data efficiently and ensure your venture remains secure in an ever-evolving digital scenario.
Think that covers the basics? Let’s drill down into some best practices that you can start implementing today to keep your data airtight.
Data Security Best Practices
With cyber threats continuously emerging, safeguarding your information has never been more critical. The implications of a breach can be severe, impacting everything from your reputation to your bottom line.
Whether you’re running a small venture or managing a large venture, comprehending and enforcing data security best practices is necessary to secure your sensitive data. Let’s learn about some pragmatic steps you can take to safeguard your information and ensure your entity’s security.
Defining Sensitive Data
Comprehending what entitles sensitive information in your entity is important. Begin by measuring the types of information you manage and their sensitivity levels. Make sure you have luminosity into where this data resides and how it flows within your systems. This step is crucial to safeguarding your information efficiently.
Establishing a Cybersecurity Policy
Create a powerful cybersecurity policy that abstracts how information should be used and safeguarded within your entity. This policy should cover everything from password management to information-sharing conventions. Appoint a Data Protection Officer (DPO) to regulate compliance and ensure everyone follows these instructions.
Building an Incident Response Plan
Prepare for the worst by having a rigid circumstance response plan in place. This plan should detail how to manage data infringement, cyber-attacks, and other security occurring. Make sure your team knows how to answer rapidly to alleviate detriment and recover from occurring efficiently.
Ensuring Secure Data Storage
Storing data safely is non-negotiable. Use encryption to safeguard sensitive information both at rest and in transit. Frequently backup your information to ensure you can recover it in case of loss or corruption. Secure data storage safeguards against illicit access and data infringement.
Limiting Access
Not everyone requires access to all information. Enforce access controls to ensure that employees only have access to the data they require to perform their jobs. Follow the principle of least advantage to minimize the risk of illicit data access.
Continuous Monitoring
Observe user activity within your systems. Continuous monitoring helps you identify suspicious behavior and potential security risks early. Use user activity monitoring solutions to track and dissect actions, ensuring your information remains safe.
Managing Third-Party Risks
Your data security elongates to third-party vendors and partners. Frequently observe their activities and hold them liable for their security practices. Ensure they follow your cybersecurity policies to safeguard your information from external risks.
By following these best practices, you can substantially improve your entity's data security, safeguard sensitive data, and minimize the risk of cyber threats.
Feeling a bit more secure now? Let’s wrap things up with a quick recap of what we’ve learned and why it matters.
Conclusion
Data security is an ever-evolving field needing constant alertness and adjustment. By comprehending the numerous types of data security, determining common risks, enforcing effective solutions, and following best practices, you can safeguard your sensitive data and maintain trust with your clients and stakeholders. Stay informed about the latest trends to keep your data security gauges latest and powerful.
Sign up at RagaAI now to receive expert insights, advanced security tools, and exclusive updates straight to your inbox. Empower your venture with the knowledge and resources needed to stay secure in the digital age.
In a world where technology shapes our daily lives, data security is more important than ever. With the augmenting amount of sensitive data stored and transmitted electronically, safeguarding this data from illicit access, breaches, and loss is paramount. This guide delves into the significance of data security, exploring the various types, common risks, efficient solutions, and best practices.
Introduction to Data Security
Data security is more vital than ever before. In today’s digital synopsis, your personal and professional data faces innumerable risks from cybercriminals and data infringement. You must prioritize safeguarding your information to avoid potential financial losses, legal consequences, and reputational damage.
Importance of Data Security
Ensuring your data is secure safeguards your seclusion, your firm’s notoriety and financial solidity. By using powerful data security measures, you can protect sensitive data against illicit access, theft, and detriment. This dynamic approach averts expensive breaches and helps maintain trust with your customers and stakeholders.
Overview of Risks, Solutions, Types, and Best Practices
Comprehending the risks associated with data security is the initial step towards efficient security. Cyber threats such as hacking, phishing, and malware can compromise your information. But don’t worry; there are solutions attainable to oppose these risks.
Types of Data Security Solutions: These include encryption, firewalls, and antivirus software. Only authorized parties can read your information with encryption, while firewalls block illicit access to your network. Antivirus software discovers and excludes vicious software.
Best Practices in Data Security: It includes frequent updates to your software, strong password policies, and employee training. Frequently updating your software to patch vulnerabilities, implementing strong password policies, and providing employee training ensures everyone is aware of potential risks and how to handle them.
By comprehending and enforcing these gauges, you can substantially improve your data security and protect your valuable data from potential threats.
Ready to dive deeper? Let’s explore the different types of data security measures to see how they can shield your information.
Looking for insights on improving your entity's security posture? Don't miss our thorough guide on Security and LLM Firewall Controls.
Types of Data Security
Data is the key to your entity’s success and if that is not safe, then it’s a big blow for the organization. That is why keeping your information safe is very important in today’s digital synopsis. Here are some key types of security gauges you can use:
Each type of data security contributes to creating a pragmatic security strategy. By comprehending and enforcing these gauges, entities can substantially reduce the risk of data breaches and ensure the integrity, confidentiality, and attainability of their data.
So, now that we know what types of security measures are out there let’s talk about the villains—common data security risks—that we need to protect against.
Prying about improving your RAG applications? Explore the power of using synthetic data to enrich RAG applications and revolutionize your AI models today!
Common Data Security Risks
Safeguarding your data isn't just a technical necessity; it's a rudimentary aspect of protecting your venture and personal data. With cyber threats becoming more sophisticated, comprehending common data security risks is vital. Whether you're a small business owner, an IT professional, or simply an individual going through the online world, staying informed about potential susceptibilities can help you enforce efficient security measures.
Ignorance isn't a delight when it comes to data security. The more you know about the risks, the better prepared you'll be to avert breaches and safeguard your sensitive data.
Below are numerous common problems faced by entities of all sizes as they attempt to safeguard sensitive information:
Human Error
Human error is one of the leading causes of data security issues. You might arbitrarily send sensitive data to the wrong recipient, misconfigure a security setting, or fall for a phishing email. It's vital to stay alert and double-check your actions to avert such mistakes.
Social Engineering Attacks
Social engineering attacks, mainly phishing, are designed to trick you into uncovering confidential data. Hackers often pose as legal organizations to gain your trust. Always validate the genuineness of unanticipated requests for sensitive information, and never click on dubious links.
Insider Threats
Insider threats can come from employees or contractors who misuse their access to your systems. This could be due to vicious intent or because an external attacker has compromised them. Frequently retrospect and restrict access to sensitive data and monitor for unusual activity.
Ransomware
Ransomware is a type of vicious software that encrypts your data and demands payment for its release. To safeguard yourself, keep your software updated, back up your data frequently, and train employees to determine dubious emails and links.
Data Loss in the Cloud
Storing data in the cloud comes with its own set of threats, including potential information loss due to misconfigurations, cyber-attacks, or service outages. Ensure you have powerful security measures in place, such as encryption and access controls, and always back up your data.
SQL Injection
SQL injection is a method where attackers insert malicious SQL code into your database queries. This can give them access to sensitive information or permit them to exploit your database. Avert this by using parameterized queries and input verification to ensure that your systems only process legal requests.
Did you get a sense of the risks? Great, let’s look into some solid solutions to fend off those pesky threats.
Want to know about Tabular Data Models? Read our comprehensive guide on the Importance of Accuracy and Reliability in Tabular Data Models.
Data Security Solutions
With cyber threats continuously developing, comprehending and enforcing powerful data security solutions is necessary to safeguard sensitive data and maintain customer trust. By assimilating comprehensive security gauges, you can ensure that your data remains confidential, maintains its integrity, and is always attainable when required.
Let’s learn about the key data security solutions that will help you bolster your defenses and keep your venture protected.
Data Encryption
When you send a secret message to a friend, you wouldn’t want anyone else to read it, right? That’s exactly what data encryption does for your data. Encryption converts your data into a code to avert illicit access. Methods such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are common. By using strong encryption, you ensure that even if data is seized, it remains unreadable without the decryption key. It’s like having a digital lock and key for your sensitive data.
Identity and Access Management
Who can access your information? Managing identities and access is vital. With Single Sign-On (SSO), you log in once and access multiple applications without re-entering credentials. This refines your experience and improves security. Multi-factor authentication (MFA) adds an auxiliary layer of protection by needing multiple validation techniques, such as a password and a fingerprint. Enforcing SSO and MFA ensures that only authorized individuals access your information, reducing the risk of infringement.
Data Masking
Ever wondered how firms safeguard sensitive data during testing and analysis? Data masking is the response. It supersedes sensitive information with functional but sensible information. Static masking and dynamic masking are two techniques used. Static masking permanently changes sensitive data in non-production environments, whereas dynamic masking hides data on-the-fly during access without altering the original data. This keeps your actual information secure while still permitting essential work to be done.
Data Loss Prevention (DLP)
Losing information can be ruinous. That’s where Data Loss Prevention (DLP) comes in. DLP methods monitor and control the data flow within your entity. Tools such as Symantec DLP and McAfee Total Protection for Data Loss Prevention help you identify, monitor, and safeguard your sensitive data. By enforcing DLP, you avert inadvertent or vicious data leaks, ensuring your data remains protected.
Security Audits
Think of security audits as a health check-up for your data security systems. Frequent security audits help you identify vulnerabilities and weaknesses. By performing these audits, you can locate and solve potential security problems before they become major issues. Tools such as Nessus and Qualys assist in scanning and reporting vulnerabilities. Staying dynamic with security audits ensures that your defenses are always up to date.
Endpoint Security
With remote work on the rise, safeguarding endpoints has never been more significant. Endpoints are devices such as laptops, tablets, and smartphones that connect to your network. Solutions like antivirus software, firewalls, and VPNs safeguard these devices. For remote work and Bring Your Own Device (BYOD) policies, ensure that you have thorough endpoint security in place to safeguard your network from potential threats.
Incident Response
What if a security infringement occurs? Having a solid incident response strategy is vital. Incident response involves preparing, detecting, and responding to security breaches. Develop a plan that includes roles, communication conventions, and recovery steps. Tools like Splunk and IBM Resilient can assist in managing incidents. A well-prepared incident response strategy minimizes damage and helps you recover quickly from breaches.
Governance, Risk, and Compliance (GRC)
Ensuring your data security practices comply with regulations is important. Governance, Risk, and Compliance (GRC) frameworks help you handle this. Governance sets the policies and procedures, risk management identifies and mitigates risks, and compliance ensures adherence to laws and standards. Tools like RSA Archer and SAP GRC streamline these processes. By enforcing GRC, you maintain a powerful security posture while meeting regulatory demands.
Clasp these data security solutions to safeguard your data efficiently and ensure your venture remains secure in an ever-evolving digital scenario.
Think that covers the basics? Let’s drill down into some best practices that you can start implementing today to keep your data airtight.
Data Security Best Practices
With cyber threats continuously emerging, safeguarding your information has never been more critical. The implications of a breach can be severe, impacting everything from your reputation to your bottom line.
Whether you’re running a small venture or managing a large venture, comprehending and enforcing data security best practices is necessary to secure your sensitive data. Let’s learn about some pragmatic steps you can take to safeguard your information and ensure your entity’s security.
Defining Sensitive Data
Comprehending what entitles sensitive information in your entity is important. Begin by measuring the types of information you manage and their sensitivity levels. Make sure you have luminosity into where this data resides and how it flows within your systems. This step is crucial to safeguarding your information efficiently.
Establishing a Cybersecurity Policy
Create a powerful cybersecurity policy that abstracts how information should be used and safeguarded within your entity. This policy should cover everything from password management to information-sharing conventions. Appoint a Data Protection Officer (DPO) to regulate compliance and ensure everyone follows these instructions.
Building an Incident Response Plan
Prepare for the worst by having a rigid circumstance response plan in place. This plan should detail how to manage data infringement, cyber-attacks, and other security occurring. Make sure your team knows how to answer rapidly to alleviate detriment and recover from occurring efficiently.
Ensuring Secure Data Storage
Storing data safely is non-negotiable. Use encryption to safeguard sensitive information both at rest and in transit. Frequently backup your information to ensure you can recover it in case of loss or corruption. Secure data storage safeguards against illicit access and data infringement.
Limiting Access
Not everyone requires access to all information. Enforce access controls to ensure that employees only have access to the data they require to perform their jobs. Follow the principle of least advantage to minimize the risk of illicit data access.
Continuous Monitoring
Observe user activity within your systems. Continuous monitoring helps you identify suspicious behavior and potential security risks early. Use user activity monitoring solutions to track and dissect actions, ensuring your information remains safe.
Managing Third-Party Risks
Your data security elongates to third-party vendors and partners. Frequently observe their activities and hold them liable for their security practices. Ensure they follow your cybersecurity policies to safeguard your information from external risks.
By following these best practices, you can substantially improve your entity's data security, safeguard sensitive data, and minimize the risk of cyber threats.
Feeling a bit more secure now? Let’s wrap things up with a quick recap of what we’ve learned and why it matters.
Conclusion
Data security is an ever-evolving field needing constant alertness and adjustment. By comprehending the numerous types of data security, determining common risks, enforcing effective solutions, and following best practices, you can safeguard your sensitive data and maintain trust with your clients and stakeholders. Stay informed about the latest trends to keep your data security gauges latest and powerful.
Sign up at RagaAI now to receive expert insights, advanced security tools, and exclusive updates straight to your inbox. Empower your venture with the knowledge and resources needed to stay secure in the digital age.
In a world where technology shapes our daily lives, data security is more important than ever. With the augmenting amount of sensitive data stored and transmitted electronically, safeguarding this data from illicit access, breaches, and loss is paramount. This guide delves into the significance of data security, exploring the various types, common risks, efficient solutions, and best practices.
Introduction to Data Security
Data security is more vital than ever before. In today’s digital synopsis, your personal and professional data faces innumerable risks from cybercriminals and data infringement. You must prioritize safeguarding your information to avoid potential financial losses, legal consequences, and reputational damage.
Importance of Data Security
Ensuring your data is secure safeguards your seclusion, your firm’s notoriety and financial solidity. By using powerful data security measures, you can protect sensitive data against illicit access, theft, and detriment. This dynamic approach averts expensive breaches and helps maintain trust with your customers and stakeholders.
Overview of Risks, Solutions, Types, and Best Practices
Comprehending the risks associated with data security is the initial step towards efficient security. Cyber threats such as hacking, phishing, and malware can compromise your information. But don’t worry; there are solutions attainable to oppose these risks.
Types of Data Security Solutions: These include encryption, firewalls, and antivirus software. Only authorized parties can read your information with encryption, while firewalls block illicit access to your network. Antivirus software discovers and excludes vicious software.
Best Practices in Data Security: It includes frequent updates to your software, strong password policies, and employee training. Frequently updating your software to patch vulnerabilities, implementing strong password policies, and providing employee training ensures everyone is aware of potential risks and how to handle them.
By comprehending and enforcing these gauges, you can substantially improve your data security and protect your valuable data from potential threats.
Ready to dive deeper? Let’s explore the different types of data security measures to see how they can shield your information.
Looking for insights on improving your entity's security posture? Don't miss our thorough guide on Security and LLM Firewall Controls.
Types of Data Security
Data is the key to your entity’s success and if that is not safe, then it’s a big blow for the organization. That is why keeping your information safe is very important in today’s digital synopsis. Here are some key types of security gauges you can use:
Each type of data security contributes to creating a pragmatic security strategy. By comprehending and enforcing these gauges, entities can substantially reduce the risk of data breaches and ensure the integrity, confidentiality, and attainability of their data.
So, now that we know what types of security measures are out there let’s talk about the villains—common data security risks—that we need to protect against.
Prying about improving your RAG applications? Explore the power of using synthetic data to enrich RAG applications and revolutionize your AI models today!
Common Data Security Risks
Safeguarding your data isn't just a technical necessity; it's a rudimentary aspect of protecting your venture and personal data. With cyber threats becoming more sophisticated, comprehending common data security risks is vital. Whether you're a small business owner, an IT professional, or simply an individual going through the online world, staying informed about potential susceptibilities can help you enforce efficient security measures.
Ignorance isn't a delight when it comes to data security. The more you know about the risks, the better prepared you'll be to avert breaches and safeguard your sensitive data.
Below are numerous common problems faced by entities of all sizes as they attempt to safeguard sensitive information:
Human Error
Human error is one of the leading causes of data security issues. You might arbitrarily send sensitive data to the wrong recipient, misconfigure a security setting, or fall for a phishing email. It's vital to stay alert and double-check your actions to avert such mistakes.
Social Engineering Attacks
Social engineering attacks, mainly phishing, are designed to trick you into uncovering confidential data. Hackers often pose as legal organizations to gain your trust. Always validate the genuineness of unanticipated requests for sensitive information, and never click on dubious links.
Insider Threats
Insider threats can come from employees or contractors who misuse their access to your systems. This could be due to vicious intent or because an external attacker has compromised them. Frequently retrospect and restrict access to sensitive data and monitor for unusual activity.
Ransomware
Ransomware is a type of vicious software that encrypts your data and demands payment for its release. To safeguard yourself, keep your software updated, back up your data frequently, and train employees to determine dubious emails and links.
Data Loss in the Cloud
Storing data in the cloud comes with its own set of threats, including potential information loss due to misconfigurations, cyber-attacks, or service outages. Ensure you have powerful security measures in place, such as encryption and access controls, and always back up your data.
SQL Injection
SQL injection is a method where attackers insert malicious SQL code into your database queries. This can give them access to sensitive information or permit them to exploit your database. Avert this by using parameterized queries and input verification to ensure that your systems only process legal requests.
Did you get a sense of the risks? Great, let’s look into some solid solutions to fend off those pesky threats.
Want to know about Tabular Data Models? Read our comprehensive guide on the Importance of Accuracy and Reliability in Tabular Data Models.
Data Security Solutions
With cyber threats continuously developing, comprehending and enforcing powerful data security solutions is necessary to safeguard sensitive data and maintain customer trust. By assimilating comprehensive security gauges, you can ensure that your data remains confidential, maintains its integrity, and is always attainable when required.
Let’s learn about the key data security solutions that will help you bolster your defenses and keep your venture protected.
Data Encryption
When you send a secret message to a friend, you wouldn’t want anyone else to read it, right? That’s exactly what data encryption does for your data. Encryption converts your data into a code to avert illicit access. Methods such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are common. By using strong encryption, you ensure that even if data is seized, it remains unreadable without the decryption key. It’s like having a digital lock and key for your sensitive data.
Identity and Access Management
Who can access your information? Managing identities and access is vital. With Single Sign-On (SSO), you log in once and access multiple applications without re-entering credentials. This refines your experience and improves security. Multi-factor authentication (MFA) adds an auxiliary layer of protection by needing multiple validation techniques, such as a password and a fingerprint. Enforcing SSO and MFA ensures that only authorized individuals access your information, reducing the risk of infringement.
Data Masking
Ever wondered how firms safeguard sensitive data during testing and analysis? Data masking is the response. It supersedes sensitive information with functional but sensible information. Static masking and dynamic masking are two techniques used. Static masking permanently changes sensitive data in non-production environments, whereas dynamic masking hides data on-the-fly during access without altering the original data. This keeps your actual information secure while still permitting essential work to be done.
Data Loss Prevention (DLP)
Losing information can be ruinous. That’s where Data Loss Prevention (DLP) comes in. DLP methods monitor and control the data flow within your entity. Tools such as Symantec DLP and McAfee Total Protection for Data Loss Prevention help you identify, monitor, and safeguard your sensitive data. By enforcing DLP, you avert inadvertent or vicious data leaks, ensuring your data remains protected.
Security Audits
Think of security audits as a health check-up for your data security systems. Frequent security audits help you identify vulnerabilities and weaknesses. By performing these audits, you can locate and solve potential security problems before they become major issues. Tools such as Nessus and Qualys assist in scanning and reporting vulnerabilities. Staying dynamic with security audits ensures that your defenses are always up to date.
Endpoint Security
With remote work on the rise, safeguarding endpoints has never been more significant. Endpoints are devices such as laptops, tablets, and smartphones that connect to your network. Solutions like antivirus software, firewalls, and VPNs safeguard these devices. For remote work and Bring Your Own Device (BYOD) policies, ensure that you have thorough endpoint security in place to safeguard your network from potential threats.
Incident Response
What if a security infringement occurs? Having a solid incident response strategy is vital. Incident response involves preparing, detecting, and responding to security breaches. Develop a plan that includes roles, communication conventions, and recovery steps. Tools like Splunk and IBM Resilient can assist in managing incidents. A well-prepared incident response strategy minimizes damage and helps you recover quickly from breaches.
Governance, Risk, and Compliance (GRC)
Ensuring your data security practices comply with regulations is important. Governance, Risk, and Compliance (GRC) frameworks help you handle this. Governance sets the policies and procedures, risk management identifies and mitigates risks, and compliance ensures adherence to laws and standards. Tools like RSA Archer and SAP GRC streamline these processes. By enforcing GRC, you maintain a powerful security posture while meeting regulatory demands.
Clasp these data security solutions to safeguard your data efficiently and ensure your venture remains secure in an ever-evolving digital scenario.
Think that covers the basics? Let’s drill down into some best practices that you can start implementing today to keep your data airtight.
Data Security Best Practices
With cyber threats continuously emerging, safeguarding your information has never been more critical. The implications of a breach can be severe, impacting everything from your reputation to your bottom line.
Whether you’re running a small venture or managing a large venture, comprehending and enforcing data security best practices is necessary to secure your sensitive data. Let’s learn about some pragmatic steps you can take to safeguard your information and ensure your entity’s security.
Defining Sensitive Data
Comprehending what entitles sensitive information in your entity is important. Begin by measuring the types of information you manage and their sensitivity levels. Make sure you have luminosity into where this data resides and how it flows within your systems. This step is crucial to safeguarding your information efficiently.
Establishing a Cybersecurity Policy
Create a powerful cybersecurity policy that abstracts how information should be used and safeguarded within your entity. This policy should cover everything from password management to information-sharing conventions. Appoint a Data Protection Officer (DPO) to regulate compliance and ensure everyone follows these instructions.
Building an Incident Response Plan
Prepare for the worst by having a rigid circumstance response plan in place. This plan should detail how to manage data infringement, cyber-attacks, and other security occurring. Make sure your team knows how to answer rapidly to alleviate detriment and recover from occurring efficiently.
Ensuring Secure Data Storage
Storing data safely is non-negotiable. Use encryption to safeguard sensitive information both at rest and in transit. Frequently backup your information to ensure you can recover it in case of loss or corruption. Secure data storage safeguards against illicit access and data infringement.
Limiting Access
Not everyone requires access to all information. Enforce access controls to ensure that employees only have access to the data they require to perform their jobs. Follow the principle of least advantage to minimize the risk of illicit data access.
Continuous Monitoring
Observe user activity within your systems. Continuous monitoring helps you identify suspicious behavior and potential security risks early. Use user activity monitoring solutions to track and dissect actions, ensuring your information remains safe.
Managing Third-Party Risks
Your data security elongates to third-party vendors and partners. Frequently observe their activities and hold them liable for their security practices. Ensure they follow your cybersecurity policies to safeguard your information from external risks.
By following these best practices, you can substantially improve your entity's data security, safeguard sensitive data, and minimize the risk of cyber threats.
Feeling a bit more secure now? Let’s wrap things up with a quick recap of what we’ve learned and why it matters.
Conclusion
Data security is an ever-evolving field needing constant alertness and adjustment. By comprehending the numerous types of data security, determining common risks, enforcing effective solutions, and following best practices, you can safeguard your sensitive data and maintain trust with your clients and stakeholders. Stay informed about the latest trends to keep your data security gauges latest and powerful.
Sign up at RagaAI now to receive expert insights, advanced security tools, and exclusive updates straight to your inbox. Empower your venture with the knowledge and resources needed to stay secure in the digital age.
In a world where technology shapes our daily lives, data security is more important than ever. With the augmenting amount of sensitive data stored and transmitted electronically, safeguarding this data from illicit access, breaches, and loss is paramount. This guide delves into the significance of data security, exploring the various types, common risks, efficient solutions, and best practices.
Introduction to Data Security
Data security is more vital than ever before. In today’s digital synopsis, your personal and professional data faces innumerable risks from cybercriminals and data infringement. You must prioritize safeguarding your information to avoid potential financial losses, legal consequences, and reputational damage.
Importance of Data Security
Ensuring your data is secure safeguards your seclusion, your firm’s notoriety and financial solidity. By using powerful data security measures, you can protect sensitive data against illicit access, theft, and detriment. This dynamic approach averts expensive breaches and helps maintain trust with your customers and stakeholders.
Overview of Risks, Solutions, Types, and Best Practices
Comprehending the risks associated with data security is the initial step towards efficient security. Cyber threats such as hacking, phishing, and malware can compromise your information. But don’t worry; there are solutions attainable to oppose these risks.
Types of Data Security Solutions: These include encryption, firewalls, and antivirus software. Only authorized parties can read your information with encryption, while firewalls block illicit access to your network. Antivirus software discovers and excludes vicious software.
Best Practices in Data Security: It includes frequent updates to your software, strong password policies, and employee training. Frequently updating your software to patch vulnerabilities, implementing strong password policies, and providing employee training ensures everyone is aware of potential risks and how to handle them.
By comprehending and enforcing these gauges, you can substantially improve your data security and protect your valuable data from potential threats.
Ready to dive deeper? Let’s explore the different types of data security measures to see how they can shield your information.
Looking for insights on improving your entity's security posture? Don't miss our thorough guide on Security and LLM Firewall Controls.
Types of Data Security
Data is the key to your entity’s success and if that is not safe, then it’s a big blow for the organization. That is why keeping your information safe is very important in today’s digital synopsis. Here are some key types of security gauges you can use:
Each type of data security contributes to creating a pragmatic security strategy. By comprehending and enforcing these gauges, entities can substantially reduce the risk of data breaches and ensure the integrity, confidentiality, and attainability of their data.
So, now that we know what types of security measures are out there let’s talk about the villains—common data security risks—that we need to protect against.
Prying about improving your RAG applications? Explore the power of using synthetic data to enrich RAG applications and revolutionize your AI models today!
Common Data Security Risks
Safeguarding your data isn't just a technical necessity; it's a rudimentary aspect of protecting your venture and personal data. With cyber threats becoming more sophisticated, comprehending common data security risks is vital. Whether you're a small business owner, an IT professional, or simply an individual going through the online world, staying informed about potential susceptibilities can help you enforce efficient security measures.
Ignorance isn't a delight when it comes to data security. The more you know about the risks, the better prepared you'll be to avert breaches and safeguard your sensitive data.
Below are numerous common problems faced by entities of all sizes as they attempt to safeguard sensitive information:
Human Error
Human error is one of the leading causes of data security issues. You might arbitrarily send sensitive data to the wrong recipient, misconfigure a security setting, or fall for a phishing email. It's vital to stay alert and double-check your actions to avert such mistakes.
Social Engineering Attacks
Social engineering attacks, mainly phishing, are designed to trick you into uncovering confidential data. Hackers often pose as legal organizations to gain your trust. Always validate the genuineness of unanticipated requests for sensitive information, and never click on dubious links.
Insider Threats
Insider threats can come from employees or contractors who misuse their access to your systems. This could be due to vicious intent or because an external attacker has compromised them. Frequently retrospect and restrict access to sensitive data and monitor for unusual activity.
Ransomware
Ransomware is a type of vicious software that encrypts your data and demands payment for its release. To safeguard yourself, keep your software updated, back up your data frequently, and train employees to determine dubious emails and links.
Data Loss in the Cloud
Storing data in the cloud comes with its own set of threats, including potential information loss due to misconfigurations, cyber-attacks, or service outages. Ensure you have powerful security measures in place, such as encryption and access controls, and always back up your data.
SQL Injection
SQL injection is a method where attackers insert malicious SQL code into your database queries. This can give them access to sensitive information or permit them to exploit your database. Avert this by using parameterized queries and input verification to ensure that your systems only process legal requests.
Did you get a sense of the risks? Great, let’s look into some solid solutions to fend off those pesky threats.
Want to know about Tabular Data Models? Read our comprehensive guide on the Importance of Accuracy and Reliability in Tabular Data Models.
Data Security Solutions
With cyber threats continuously developing, comprehending and enforcing powerful data security solutions is necessary to safeguard sensitive data and maintain customer trust. By assimilating comprehensive security gauges, you can ensure that your data remains confidential, maintains its integrity, and is always attainable when required.
Let’s learn about the key data security solutions that will help you bolster your defenses and keep your venture protected.
Data Encryption
When you send a secret message to a friend, you wouldn’t want anyone else to read it, right? That’s exactly what data encryption does for your data. Encryption converts your data into a code to avert illicit access. Methods such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are common. By using strong encryption, you ensure that even if data is seized, it remains unreadable without the decryption key. It’s like having a digital lock and key for your sensitive data.
Identity and Access Management
Who can access your information? Managing identities and access is vital. With Single Sign-On (SSO), you log in once and access multiple applications without re-entering credentials. This refines your experience and improves security. Multi-factor authentication (MFA) adds an auxiliary layer of protection by needing multiple validation techniques, such as a password and a fingerprint. Enforcing SSO and MFA ensures that only authorized individuals access your information, reducing the risk of infringement.
Data Masking
Ever wondered how firms safeguard sensitive data during testing and analysis? Data masking is the response. It supersedes sensitive information with functional but sensible information. Static masking and dynamic masking are two techniques used. Static masking permanently changes sensitive data in non-production environments, whereas dynamic masking hides data on-the-fly during access without altering the original data. This keeps your actual information secure while still permitting essential work to be done.
Data Loss Prevention (DLP)
Losing information can be ruinous. That’s where Data Loss Prevention (DLP) comes in. DLP methods monitor and control the data flow within your entity. Tools such as Symantec DLP and McAfee Total Protection for Data Loss Prevention help you identify, monitor, and safeguard your sensitive data. By enforcing DLP, you avert inadvertent or vicious data leaks, ensuring your data remains protected.
Security Audits
Think of security audits as a health check-up for your data security systems. Frequent security audits help you identify vulnerabilities and weaknesses. By performing these audits, you can locate and solve potential security problems before they become major issues. Tools such as Nessus and Qualys assist in scanning and reporting vulnerabilities. Staying dynamic with security audits ensures that your defenses are always up to date.
Endpoint Security
With remote work on the rise, safeguarding endpoints has never been more significant. Endpoints are devices such as laptops, tablets, and smartphones that connect to your network. Solutions like antivirus software, firewalls, and VPNs safeguard these devices. For remote work and Bring Your Own Device (BYOD) policies, ensure that you have thorough endpoint security in place to safeguard your network from potential threats.
Incident Response
What if a security infringement occurs? Having a solid incident response strategy is vital. Incident response involves preparing, detecting, and responding to security breaches. Develop a plan that includes roles, communication conventions, and recovery steps. Tools like Splunk and IBM Resilient can assist in managing incidents. A well-prepared incident response strategy minimizes damage and helps you recover quickly from breaches.
Governance, Risk, and Compliance (GRC)
Ensuring your data security practices comply with regulations is important. Governance, Risk, and Compliance (GRC) frameworks help you handle this. Governance sets the policies and procedures, risk management identifies and mitigates risks, and compliance ensures adherence to laws and standards. Tools like RSA Archer and SAP GRC streamline these processes. By enforcing GRC, you maintain a powerful security posture while meeting regulatory demands.
Clasp these data security solutions to safeguard your data efficiently and ensure your venture remains secure in an ever-evolving digital scenario.
Think that covers the basics? Let’s drill down into some best practices that you can start implementing today to keep your data airtight.
Data Security Best Practices
With cyber threats continuously emerging, safeguarding your information has never been more critical. The implications of a breach can be severe, impacting everything from your reputation to your bottom line.
Whether you’re running a small venture or managing a large venture, comprehending and enforcing data security best practices is necessary to secure your sensitive data. Let’s learn about some pragmatic steps you can take to safeguard your information and ensure your entity’s security.
Defining Sensitive Data
Comprehending what entitles sensitive information in your entity is important. Begin by measuring the types of information you manage and their sensitivity levels. Make sure you have luminosity into where this data resides and how it flows within your systems. This step is crucial to safeguarding your information efficiently.
Establishing a Cybersecurity Policy
Create a powerful cybersecurity policy that abstracts how information should be used and safeguarded within your entity. This policy should cover everything from password management to information-sharing conventions. Appoint a Data Protection Officer (DPO) to regulate compliance and ensure everyone follows these instructions.
Building an Incident Response Plan
Prepare for the worst by having a rigid circumstance response plan in place. This plan should detail how to manage data infringement, cyber-attacks, and other security occurring. Make sure your team knows how to answer rapidly to alleviate detriment and recover from occurring efficiently.
Ensuring Secure Data Storage
Storing data safely is non-negotiable. Use encryption to safeguard sensitive information both at rest and in transit. Frequently backup your information to ensure you can recover it in case of loss or corruption. Secure data storage safeguards against illicit access and data infringement.
Limiting Access
Not everyone requires access to all information. Enforce access controls to ensure that employees only have access to the data they require to perform their jobs. Follow the principle of least advantage to minimize the risk of illicit data access.
Continuous Monitoring
Observe user activity within your systems. Continuous monitoring helps you identify suspicious behavior and potential security risks early. Use user activity monitoring solutions to track and dissect actions, ensuring your information remains safe.
Managing Third-Party Risks
Your data security elongates to third-party vendors and partners. Frequently observe their activities and hold them liable for their security practices. Ensure they follow your cybersecurity policies to safeguard your information from external risks.
By following these best practices, you can substantially improve your entity's data security, safeguard sensitive data, and minimize the risk of cyber threats.
Feeling a bit more secure now? Let’s wrap things up with a quick recap of what we’ve learned and why it matters.
Conclusion
Data security is an ever-evolving field needing constant alertness and adjustment. By comprehending the numerous types of data security, determining common risks, enforcing effective solutions, and following best practices, you can safeguard your sensitive data and maintain trust with your clients and stakeholders. Stay informed about the latest trends to keep your data security gauges latest and powerful.
Sign up at RagaAI now to receive expert insights, advanced security tools, and exclusive updates straight to your inbox. Empower your venture with the knowledge and resources needed to stay secure in the digital age.
Subscribe to our newsletter to never miss an update
Subscribe to our newsletter to never miss an update
Other articles



Exploring Intelligent Agents in AI

Rehan Asif
Jan 3, 2025
Read the article




Understanding What AI Red Teaming Means for Generative Models
Jigar Gupta
Dec 30, 2024
Read the article




RAG vs Fine-Tuning: Choosing the Best AI Learning Technique

Jigar Gupta
Dec 27, 2024
Read the article




Understanding NeMo Guardrails: A Toolkit for LLM Security

Rehan Asif
Dec 24, 2024
Read the article




Understanding Differences in Large vs Small Language Models (LLM vs SLM)

Rehan Asif
Dec 21, 2024
Read the article




Understanding What an AI Agent is: Key Applications and Examples

Jigar Gupta
Dec 17, 2024
Read the article




Prompt Engineering and Retrieval Augmented Generation (RAG)

Jigar Gupta
Dec 12, 2024
Read the article




Exploring How Multimodal Large Language Models Work

Rehan Asif
Dec 9, 2024
Read the article



Evaluating and Enhancing LLM-as-a-Judge with Automated Tools

Rehan Asif
Dec 6, 2024
Read the article




Optimizing Performance and Cost by Caching LLM Queries

Rehan Asif
Dec 3, 2024
Read the article




LoRA vs RAG: Full Model Fine-Tuning in Large Language Models

Jigar Gupta
Nov 30, 2024
Read the article



Steps to Train LLM on Personal Data

Rehan Asif
Nov 28, 2024
Read the article




Step by Step Guide to Building RAG-based LLM Applications with Examples

Rehan Asif
Nov 27, 2024
Read the article



Building AI Agentic Workflows with Multi-Agent Collaboration

Jigar Gupta
Nov 25, 2024
Read the article




Top Large Language Models (LLMs) in 2024

Rehan Asif
Nov 22, 2024
Read the article




Creating Apps with Large Language Models

Rehan Asif
Nov 21, 2024
Read the article




Best Practices In Data Governance For AI

Jigar Gupta
Nov 17, 2024
Read the article



Transforming Conversational AI with Large Language Models

Rehan Asif
Nov 15, 2024
Read the article




Deploying Generative AI Agents with Local LLMs

Rehan Asif
Nov 13, 2024
Read the article




Exploring Different Types of AI Agents with Key Examples

Jigar Gupta
Nov 11, 2024
Read the article




Creating Your Own Personal LLM Agents: Introduction to Implementation

Rehan Asif
Nov 8, 2024
Read the article




Exploring Agentic AI Architecture and Design Patterns

Jigar Gupta
Nov 6, 2024
Read the article




Building Your First LLM Agent Framework Application

Rehan Asif
Nov 4, 2024
Read the article




Multi-Agent Design and Collaboration Patterns

Rehan Asif
Nov 1, 2024
Read the article




Creating Your Own LLM Agent Application from Scratch

Rehan Asif
Oct 30, 2024
Read the article




Solving LLM Token Limit Issues: Understanding and Approaches

Rehan Asif
Oct 27, 2024
Read the article



Understanding the Impact of Inference Cost on Generative AI Adoption

Jigar Gupta
Oct 24, 2024
Read the article




Data Security: Risks, Solutions, Types and Best Practices

Jigar Gupta
Oct 21, 2024
Read the article




Getting Contextual Understanding Right for RAG Applications

Jigar Gupta
Oct 19, 2024
Read the article




Understanding Data Fragmentation and Strategies to Overcome It

Jigar Gupta
Oct 16, 2024
Read the article



Understanding Techniques and Applications for Grounding LLMs in Data

Rehan Asif
Oct 13, 2024
Read the article




Advantages Of Using LLMs For Rapid Application Development

Rehan Asif
Oct 10, 2024
Read the article



Understanding React Agent in LangChain Engineering

Rehan Asif
Oct 7, 2024
Read the article



Using RagaAI Catalyst to Evaluate LLM Applications

Gaurav Agarwal
Oct 4, 2024
Read the article




Step-by-Step Guide on Training Large Language Models

Rehan Asif
Oct 1, 2024
Read the article



Understanding LLM Agent Architecture

Rehan Asif
Aug 19, 2024
Read the article




Understanding the Need and Possibilities of AI Guardrails Today

Jigar Gupta
Aug 19, 2024
Read the article




How to Prepare Quality Dataset for LLM Training

Rehan Asif
Aug 14, 2024
Read the article




Understanding Multi-Agent LLM Framework and Its Performance Scaling

Rehan Asif
Aug 15, 2024
Read the article



Understanding and Tackling Data Drift: Causes, Impact, and Automation Strategies

Jigar Gupta
Aug 14, 2024
Read the article




Introducing RagaAI Catalyst: Best in class automated LLM evaluation with 93% Human Alignment
Gaurav Agarwal
Jul 15, 2024
Read the article




Key Pillars and Techniques for LLM Observability and Monitoring

Rehan Asif
Jul 24, 2024
Read the article



Introduction to What is LLM Agents and How They Work?

Rehan Asif
Jul 24, 2024
Read the article




Analysis of the Large Language Model Landscape Evolution

Rehan Asif
Jul 24, 2024
Read the article




Marketing Success With Retrieval Augmented Generation (RAG) Platforms

Jigar Gupta
Jul 24, 2024
Read the article




Developing AI Agent Strategies Using GPT

Jigar Gupta
Jul 24, 2024
Read the article




Identifying Triggers for Retraining AI Models to Maintain Performance

Jigar Gupta
Jul 16, 2024
Read the article



Agentic Design Patterns In LLM-Based Applications

Rehan Asif
Jul 16, 2024
Read the article



Generative AI And Document Question Answering With LLMs

Jigar Gupta
Jul 15, 2024
Read the article




How to Fine-Tune ChatGPT for Your Use Case - Step by Step Guide

Jigar Gupta
Jul 15, 2024
Read the article




Security and LLM Firewall Controls

Rehan Asif
Jul 15, 2024
Read the article




Understanding the Use of Guardrail Metrics in Ensuring LLM Safety

Rehan Asif
Jul 13, 2024
Read the article




Exploring the Future of LLM and Generative AI Infrastructure

Rehan Asif
Jul 13, 2024
Read the article




Comprehensive Guide to RLHF and Fine Tuning LLMs from Scratch

Rehan Asif
Jul 13, 2024
Read the article




Using Synthetic Data To Enrich RAG Applications

Jigar Gupta
Jul 13, 2024
Read the article




Comparing Different Large Language Model (LLM) Frameworks

Rehan Asif
Jul 12, 2024
Read the article




Integrating AI Models with Continuous Integration Systems

Jigar Gupta
Jul 12, 2024
Read the article




Understanding Retrieval Augmented Generation for Large Language Models: A Survey

Jigar Gupta
Jul 12, 2024
Read the article




Leveraging AI For Enhanced Retail Customer Experiences

Jigar Gupta
Jul 1, 2024
Read the article




Enhancing Enterprise Search Using RAG and LLMs

Rehan Asif
Jul 1, 2024
Read the article



Importance of Accuracy and Reliability in Tabular Data Models

Jigar Gupta
Jul 1, 2024
Read the article




Information Retrieval And LLMs: RAG Explained

Rehan Asif
Jul 1, 2024
Read the article




Introduction to LLM Powered Autonomous Agents

Rehan Asif
Jul 1, 2024
Read the article




Guide on Unified Multi-Dimensional LLM Evaluation and Benchmark Metrics

Rehan Asif
Jul 1, 2024
Read the article




Innovations In AI For Healthcare

Jigar Gupta
Jun 24, 2024
Read the article




Implementing AI-Driven Inventory Management For The Retail Industry

Jigar Gupta
Jun 24, 2024
Read the article




Practical Retrieval Augmented Generation: Use Cases And Impact

Jigar Gupta
Jun 24, 2024
Read the article




LLM Pre-Training and Fine-Tuning Differences

Rehan Asif
Jun 23, 2024
Read the article




20 LLM Project Ideas For Beginners Using Large Language Models

Rehan Asif
Jun 23, 2024
Read the article




Understanding LLM Parameters: Tuning Top-P, Temperature And Tokens

Rehan Asif
Jun 23, 2024
Read the article




Understanding Large Action Models In AI

Rehan Asif
Jun 23, 2024
Read the article




Building And Implementing Custom LLM Guardrails

Rehan Asif
Jun 12, 2024
Read the article




Understanding LLM Alignment: A Simple Guide

Rehan Asif
Jun 12, 2024
Read the article



Practical Strategies For Self-Hosting Large Language Models

Rehan Asif
Jun 12, 2024
Read the article



Practical Guide For Deploying LLMs In Production

Rehan Asif
Jun 12, 2024
Read the article




The Impact Of Generative Models On Content Creation

Jigar Gupta
Jun 12, 2024
Read the article




Implementing Regression Tests In AI Development

Jigar Gupta
Jun 12, 2024
Read the article




In-Depth Case Studies in AI Model Testing: Exploring Real-World Applications and Insights

Jigar Gupta
Jun 11, 2024
Read the article




Techniques and Importance of Stress Testing AI Systems

Jigar Gupta
Jun 11, 2024
Read the article




Navigating Global AI Regulations and Standards

Rehan Asif
Jun 10, 2024
Read the article




The Cost of Errors In AI Application Development

Rehan Asif
Jun 10, 2024
Read the article




Best Practices In Data Governance For AI

Rehan Asif
Jun 10, 2024
Read the article




Success Stories And Case Studies Of AI Adoption Across Industries

Jigar Gupta
May 1, 2024
Read the article



Exploring The Frontiers Of Deep Learning Applications

Jigar Gupta
May 1, 2024
Read the article




Integration Of RAG Platforms With Existing Enterprise Systems

Jigar Gupta
Apr 30, 2024
Read the article




Multimodal LLMS Using Image And Text

Rehan Asif
Apr 30, 2024
Read the article




Understanding ML Model Monitoring In Production

Rehan Asif
Apr 30, 2024
Read the article




Strategic Approach To Testing AI-Powered Applications And Systems

Rehan Asif
Apr 30, 2024
Read the article




Navigating GDPR Compliance for AI Applications

Rehan Asif
Apr 26, 2024
Read the article



The Impact of AI Governance on Innovation and Development Speed

Rehan Asif
Apr 26, 2024
Read the article



Best Practices For Testing Computer Vision Models

Jigar Gupta
Apr 25, 2024
Read the article



Building Low-Code LLM Apps with Visual Programming

Rehan Asif
Apr 26, 2024
Read the article




Understanding AI regulations In Finance

Akshat Gupta
Apr 26, 2024
Read the article




Compliance Automation: Getting Started with Regulatory Management

Akshat Gupta
Apr 25, 2024
Read the article




Practical Guide to Fine-Tuning OpenAI GPT Models Using Python

Rehan Asif
Apr 24, 2024
Read the article




Comparing Different Large Language Models (LLM)

Rehan Asif
Apr 23, 2024
Read the article




Evaluating Large Language Models: Methods And Metrics

Rehan Asif
Apr 22, 2024
Read the article




Significant AI Errors, Mistakes, Failures, and Flaws Companies Encounter

Akshat Gupta
Apr 21, 2024
Read the article




Challenges and Strategies for Implementing Enterprise LLM

Rehan Asif
Apr 20, 2024
Read the article




Enhancing Computer Vision with Synthetic Data: Advantages and Generation Techniques

Jigar Gupta
Apr 20, 2024
Read the article



Building Trust In Artificial Intelligence Systems

Akshat Gupta
Apr 19, 2024
Read the article




A Brief Guide To LLM Parameters: Tuning and Optimization

Rehan Asif
Apr 18, 2024
Read the article




Unlocking The Potential Of Computer Vision Testing: Key Techniques And Tools

Jigar Gupta
Apr 17, 2024
Read the article




Understanding AI Regulatory Compliance And Its Importance

Akshat Gupta
Apr 16, 2024
Read the article




Understanding The Basics Of AI Governance

Akshat Gupta
Apr 15, 2024
Read the article




Understanding Prompt Engineering: A Guide

Rehan Asif
Apr 15, 2024
Read the article



Examples And Strategies To Mitigate AI Bias In Real-Life

Akshat Gupta
Apr 14, 2024
Read the article




Understanding The Basics Of LLM Fine-tuning With Custom Data

Rehan Asif
Apr 13, 2024
Read the article



Overview Of Key Concepts In AI Safety And Security

Jigar Gupta
Apr 12, 2024
Read the article




Understanding Hallucinations In LLMs

Rehan Asif
Apr 7, 2024
Read the article




Demystifying FDA's Approach to AI/ML in Healthcare: Your Ultimate Guide

Gaurav Agarwal
Apr 4, 2024
Read the article




Navigating AI Governance in Aerospace Industry

Akshat Gupta
Apr 3, 2024
Read the article




The White House Executive Order on Safe and Trustworthy AI

Jigar Gupta
Mar 29, 2024
Read the article




The EU AI Act - All you need to know
Akshat Gupta
Mar 27, 2024
Read the article



Enhancing Edge AI with RagaAI Integration on NVIDIA Metropolis

Siddharth Jain
Mar 15, 2024
Read the article




RagaAI releases the most comprehensive open-source LLM Evaluation and Guardrails package

Gaurav Agarwal
Mar 7, 2024
Read the article
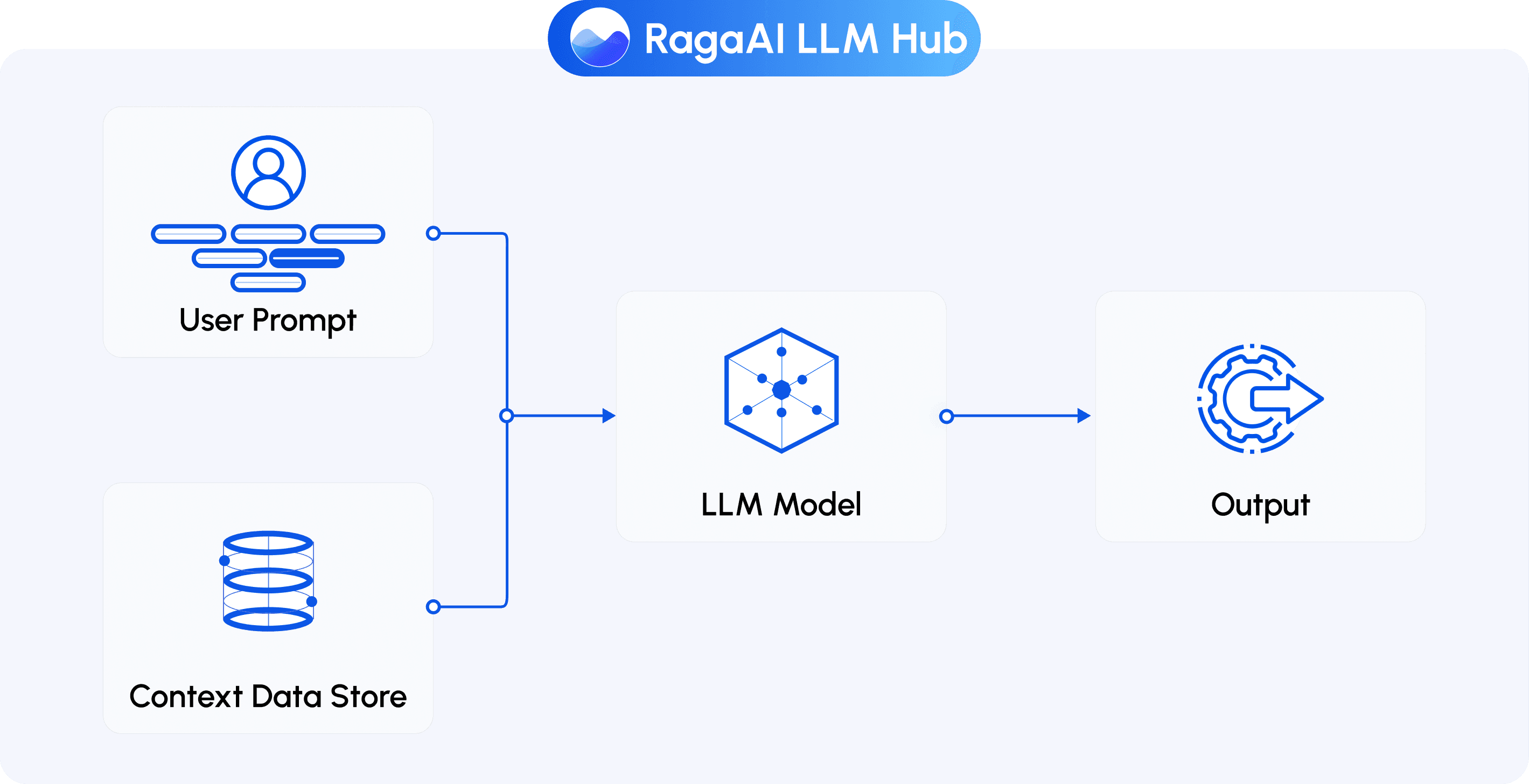



A Guide to Evaluating LLM Applications and enabling Guardrails using Raga-LLM-Hub

Rehan Asif
Mar 7, 2024
Read the article




Identifying edge cases within CelebA Dataset using RagaAI testing Platform

Rehan Asif
Feb 15, 2024
Read the article
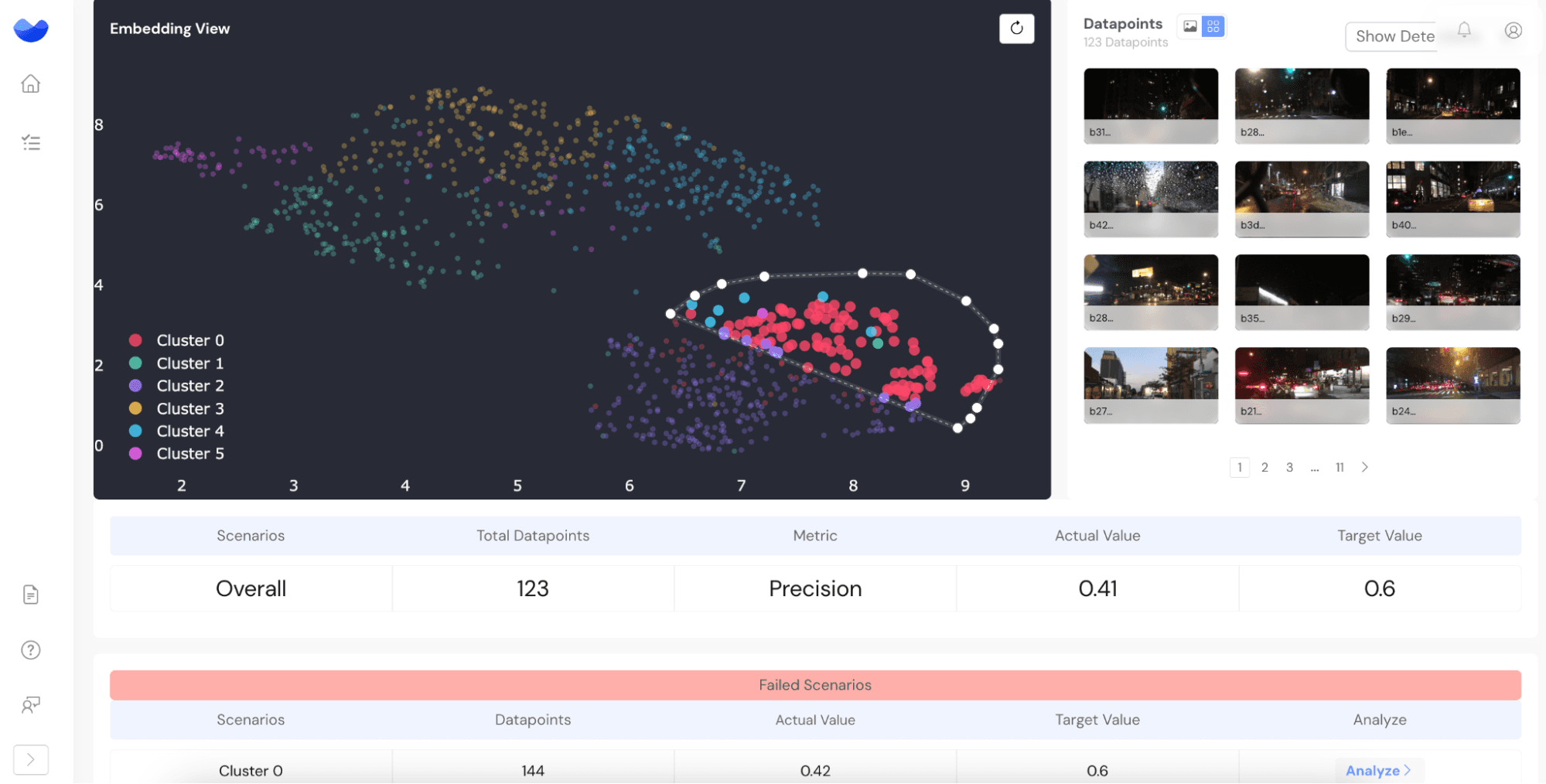



How to Detect and Fix AI Issues with RagaAI

Jigar Gupta
Feb 16, 2024
Read the article




Detection of Labelling Issue in CIFAR-10 Dataset using RagaAI Platform
Rehan Asif
Feb 5, 2024
Read the article




RagaAI emerges from Stealth with the most Comprehensive Testing Platform for AI
Gaurav Agarwal
Jan 23, 2024
Read the article




AI’s Missing Piece: Comprehensive AI Testing

Gaurav Agarwal
Jan 11, 2024
Read the article




Introducing RagaAI - The Future of AI Testing
Jigar Gupta
Jan 14, 2024
Read the article




Introducing RagaAI DNA: The Multi-modal Foundation Model for AI Testing
Rehan Asif
Jan 13, 2024
Read the article
Get Started With RagaAI®
Book a Demo
Schedule a call with AI Testing Experts

Get Started With RagaAI®
Book a Demo
Schedule a call with AI Testing Experts





